Cheaters Beware: Exposing the Truth
Stay informed about deceitful behaviors and protect yourself from betrayal.
Why Secure Decentralized Platforms Are Like the Modern-Day Fortresses for Your Digital Life
Discover how secure decentralized platforms act as fortresses for your digital life, protecting your data like never before!
Exploring the Fortified Nature of Secure Decentralized Platforms
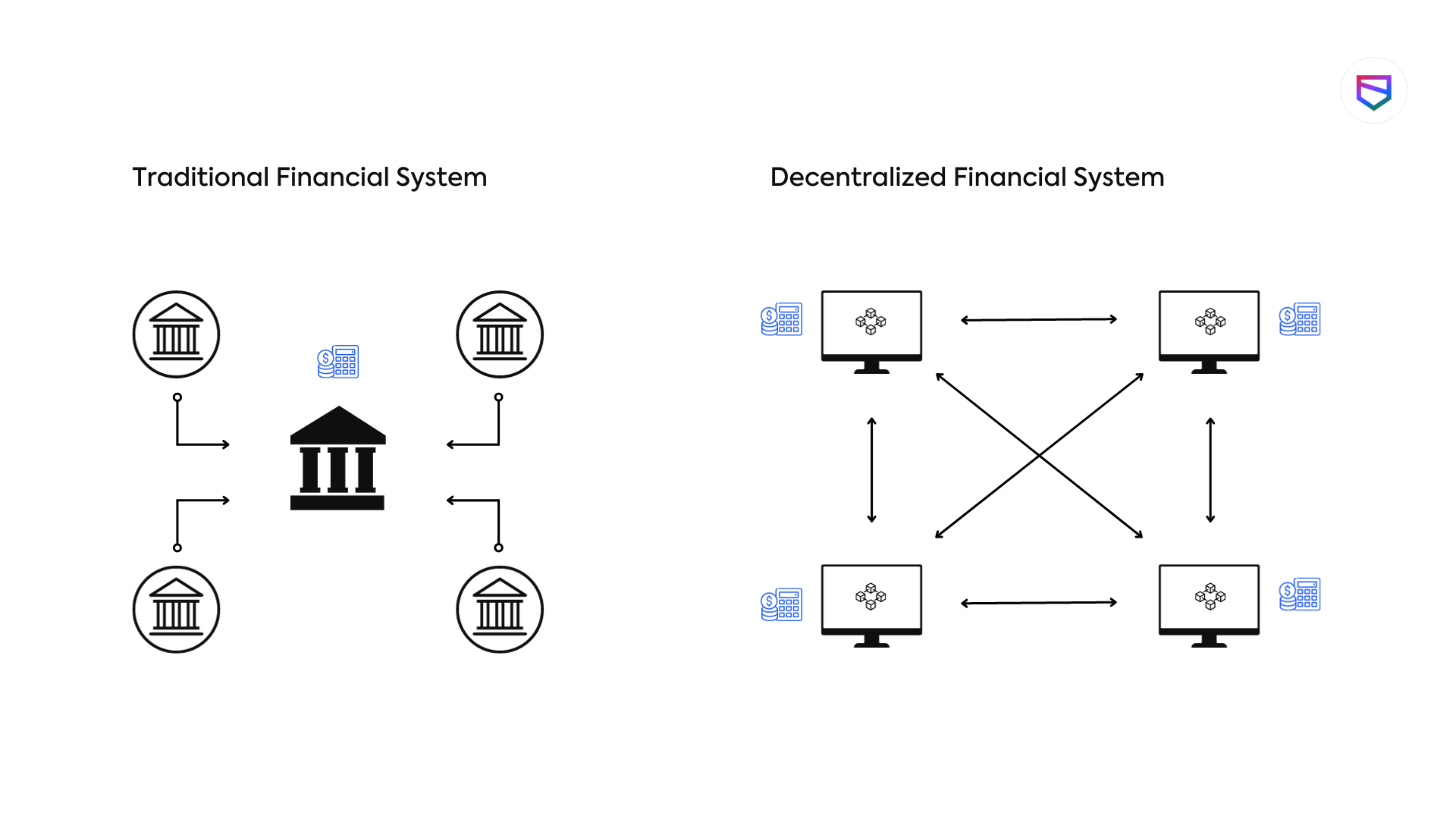
The evolution of technology has given rise to secure decentralized platforms that enhance data integrity and user privacy. These platforms leverage blockchain and distributed ledger technologies to eliminate single points of failure, ensuring that no single entity has control over the data. This fortified nature of decentralized systems not only fortifies data security but also empowers users, promoting transparency and trust. As organizations explore these innovations, understanding the architecture behind secure decentralized platforms becomes crucial in maximizing their potential and mitigating risks associated with centralization.
Furthermore, the fortified nature of secure decentralized platforms opens new avenues for applications across various industries. By decentralizing data management and employing robust cryptographic techniques, businesses can safeguard sensitive information while also ensuring compliance with data protection regulations. Consider these key benefits of secure decentralized platforms:
- Enhanced security from cyber threats
- Increased user autonomy and privacy
- Reduced operational costs through improved efficiency
Counter-Strike is a popular tactical first-person shooter game that has captivated gamers worldwide since its release. Players engage in team-based action, where one side takes on the role of terrorists and the other as counter-terrorists. For players looking to enhance their gaming experience, they can find exciting offers by checking out the cryptocasino.com promo code. With its competitive gameplay and strategic depth, Counter-Strike remains a staple in the esports scene.
How Secure Decentralized Platforms Protect Your Digital Identity
In today’s digital landscape, preserving your online privacy has never been more crucial. Decentralized platforms offer a revolutionary way to protect your digital identity by enabling users to have full control over their personal data. Unlike traditional centralized systems that store user information on a single server, decentralized platforms distribute data across a network of nodes, ensuring that no single entity can access or manipulate your information without your consent. This architecture significantly reduces the risk of data breaches and identity theft, as hackers face a more challenging environment when attempting to breach multiple nodes.
Moreover, many decentralized platforms utilize blockchain technology, which adds an additional layer of security through its immutable ledger. Users can verify transactions and changes to their data in real-time, creating a transparent yet secure environment for digital interaction. By embracing these technologies, individuals can protect their digital identity while enjoying the benefits of online platforms, such as social networking, e-commerce, and cloud storage, without compromising their personal information. This shift not only safeguards individual privacy but also empowers users to take charge of their online presence.
Are Decentralized Platforms the Future of Online Security?
As we navigate an increasingly digital world, the concern for online security has become paramount. Traditional centralized platforms often fall prey to cyberattacks, data breaches, and unauthorized access, leading to the critical question: Are decentralized platforms the future of online security? By distributing data across multiple nodes rather than relying on a single point of failure, these platforms enhance resilience against attacks. Decentralization not only reduces the risk of large-scale data breaches but also empowers users, giving them greater control over their information.
In addition to heightened security, decentralized platforms often incorporate innovative technologies such as blockchain, which further strengthens user trust through transparency and immutability. Moreover, platforms based on smart contracts can automate security protocols, ensuring that user data remains protected without the need for intermediaries. As society increasingly prioritizes privacy and security, it is evident that the shift towards decentralized systems might be more than a trend; it could represent a pivotal moment in the evolution of online security.